Token Authentication
When scripting against the APIs it's often better to use token authentication (versus creating a user). With the benefit of tokens having a built in expiry date.
Generate a token from a policy
Tokens are generally created from a specific policy.
supctl
supctl do strongbox token create-token --policies registry-push --ttl 4h
accessor: d468d35d-03af-433d-a7cf-ab7374c6f692
token: 96b08b7c-7310-4805-8f27-2591816be019
creation-time: 2024-11-18T09:57:57.933330Z
UI
The same operation can be accomplished in the UI.
Go to policies in the main menu and click the policy action menu.
| Select Generate Token | Set desired TTL | Generated Token |
|---|---|---|
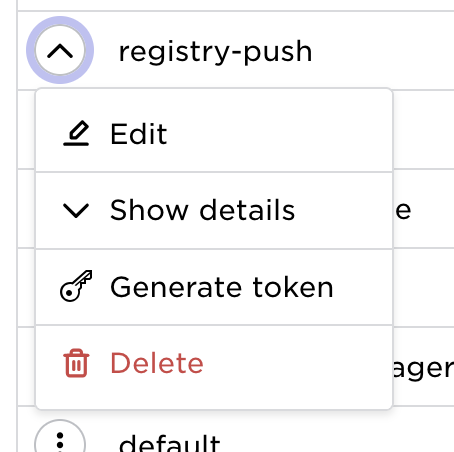 | 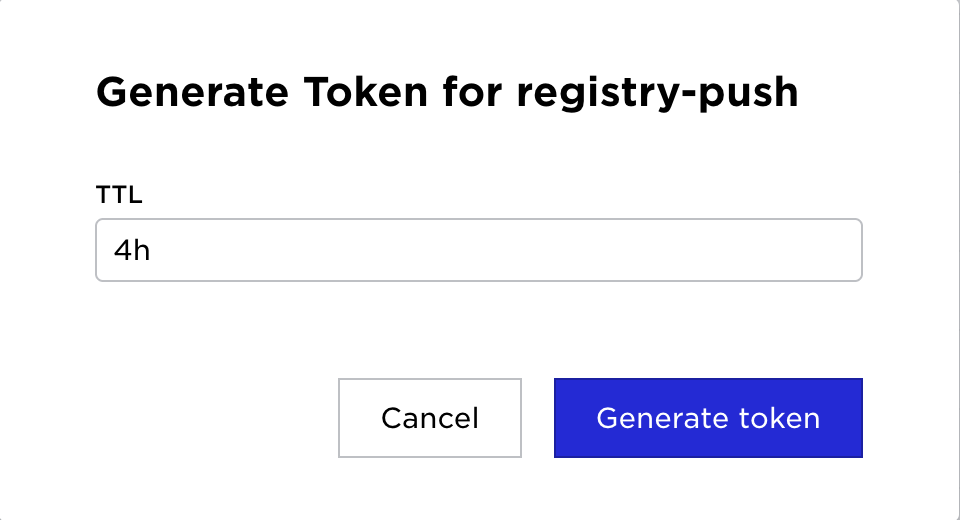 | 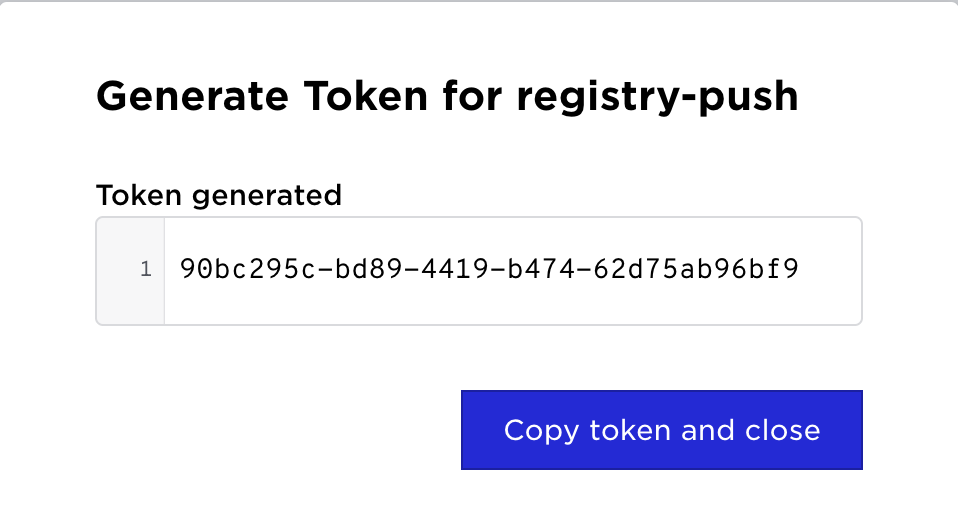 |
Using tokens
supctl
The token can be passed to supctl by using -t
supctl -t 96b08b7c-7310-4805-8f27-2591816be019 list system sites
API
The token generated can be used in API calls by setting the Authorization header, e.g.
Authorization: Bearer 96b08b7c-7310-4805-8f27-2591816be019
Docker
To authenticate against a Control Tower registry, set the password to the acquired token.
docker login registry.my-env.my-org.avassa.net --username any --password 96b08b7c-7310-4805-8f27-2591816be019