Port forwarding
The Avassa system provides a way to forward connections to a local port to an
application service running in the Avassa system, akin to ssh -L behaviour of
the OpenSSH client.
Connect to a port open locally in the service
If the intention is to connect to a server running in an application in the Avassa system, then the following command may be used:
supctl do -s stockholm-sergel applications popcorn-controller service-instances \
popcorn-controller-service-1 connect tcp 443 --bind 8443
This example allows us to connect to the service instance
popcorn-controller-service-1 which runs on the edge site stockholm-sergel
as a part of application popcorn-controller. The supctl command will listen
on port tcp/8443 locally and forward any local connections to port tcp/443
on 127.0.0.1 inside the service instance. Note that it does not matter which
container runs the server: if there are multiple containers running as part of
the same service instance, they would all be sharing the same TCP/IP stack.
Proxy connections to a remote host
It is possible to proxy connections to a remote host accessible from a service running in the Avassa system via such service. This could be useful, for example, to debug devices on the same local network as the Avassa host.
supctl do -s stockholm-sergel applications popcorn-controller service-instances \
popcorn-controller-service-1 connect tcp 443 --ip-address 192.0.2.11 --bind 8443
In this example we are connecting to the IP address 192.0.2.11 on port
tcp/443. The TCP connection is initiated from the service instance
popcorn-controller-service-1 which runs on the edge site stockholm-sergel
as a part of application popcorn-controller. The supctl command listens to
port tcp/8443 locally and forwards any connections to this destination.
The IP address must be provided in numeric form, the command does not perform
DNS resolution. If the IP address is unknown beforehand, and only the domain
name is known, then it must first be resolved remotely, for example using the
exec command as follows:
supctl do -s stockholm-sergel applications popcorn-controller service-instances \
popcorn-controller-service-1 containers kettle-popper-manager \
exec 'nslookup destination.example'
Netcat mode
In the above examples the supctl command listens on a local port and forwards
incoming connections to the remote service. Instead of listening on a local port
the supctl command can print received bytes on the stdout and send the
input from stdin to the remote destination, akin to the nc command. In order
to use the netcat mode omit the --bind flag from the examples above.
Details of implementation
The communication channel is initiated via a secure WebSocket towards the Control Tower, and then forwarded via the infrastructure network to the requested Edge site, illustrated below.
The number of intermediate hops and extra processing implies increased latency and bandwidth limitations, so this communication method is most appropriate for tasks such as testing and debugging, and not for production use.
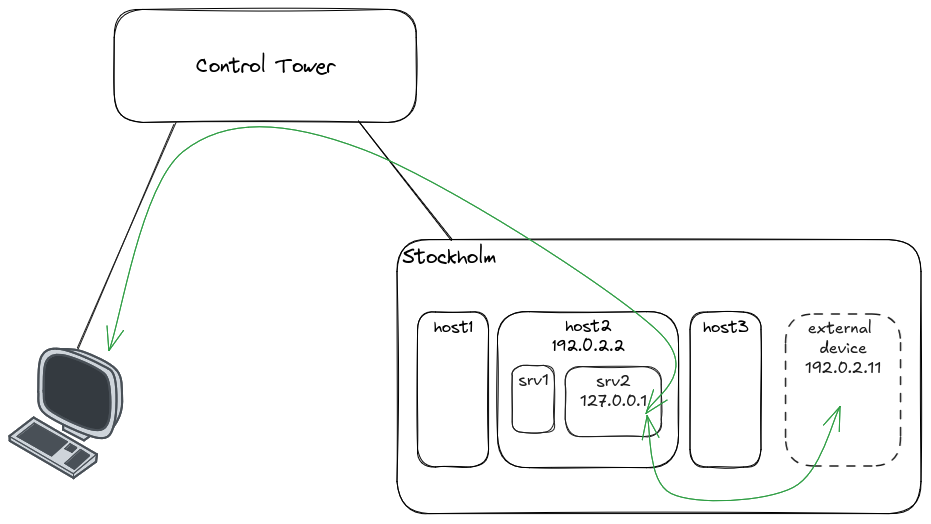
On the target host the Edge Enforcer agent initiates the connection from the
target service's network namespace, which means that the 127.0.0.1 address
represents the service itself. For any external connection
the source IP address will be the service's IP address determined according to
the routing table.